Ransomware Detection
Datto RMM is a secure and fully-featured cloud platform enabling MSPs to remotely monitor, manage, and support their endpoints, and it now also provides an extra layer of security with native Ransomware Detection. Datto RMM Ransomware Detection monitors for the existence of crypto-ransomware on endpoints using proprietary behavioral analysis of files and alerts you when a device is infected. Once ransomware is detected, Datto RMM can isolate the device and attempt to stop suspected ransomware processes to prevent the ransomware from spreading.
This topic provides an overview of Ransomware Detection in Datto RMM and answers questions frequently asked by our partners.
Key benefits
- Know about ransomware infections instantly. Instead of waiting for a user to report the issue, Datto RMM will notify technicians at the moment files get encrypted by the ransomware. This will provide more time to respond and possibly prevent the spread. The screenshot below shows an example of a Datto RMM alert generated when ransomware is detected on a device.
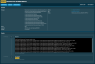
- Easily monitor using policy-driven configuration. Datto RMM’s powerful policy-driven approach allows MSPs to easily monitor targeted devices at scale for the presence of ransomware. Integrations with key MSP tools, such as Autotask PSA or ConnectWise Manage, along with email notification options, ensure that the right resources can be notified immediately if ransomware is detected.
- Prevent spreading of ransomware with automatic network isolation and termination of ransomware processes. Once ransomware is detected, you can have the Agent isolate the affected device from the network and attempt to stop suspected ransomware processes to prevent further spread of the ransomware to other devices.
- Remediate issues remotely. Devices automatically isolated from the network can still contact Datto RMM, allowing technicians to take effective action to resolve the issue.
- Recover with Datto Continuity products. When Datto RMM is integrated with Datto BCDR, technicians can quickly recover from the ransomware outbreak by restoring a device to a previous state.
Requirements
- You must have an active Datto RMM subscription or trial.
- Ransomware Detection must be enabled.
NOTE The Ransomware monitor requires an additional license before it can be used. Refer to Enable Ransomware Detection and add licenses.
- You must have the relevant permissions to add a Ransomware monitor to a device or to a Monitoring policy.
- Devices must be managed devices. Ransomware Detection is not available for OnDemand devices.
- The Ransomware monitor is only available in the New UI.
Supported devices
The Ransomware monitor can be applied on all supported Windows devices. Refer to Windows.
Ransomware monitor features
You can create a Ransomware monitor as a standalone monitor added to individual devices or as part of a Monitoring policy. The monitor includes the following features:
- Alert details that include options such as configuring monitored locations and paths, excluding file extensions, and setting alert priority. These criteria specify what the monitor looks for before an alert is created.
- Response details that include options such as isolating the affected device from the network or configuring a custom response component, attempting to stop suspected ransomware processes, ticket creation, and email response.
For information about how to create a monitor in the New UI and how to specify the details of a Ransomware monitor, refer to Monitors - New UI and Ransomware monitor.
For information about how to create a policy in the New UI and how to specify the details of a Monitoring policy, refer to Policies - New UI and Monitoring policy.
FAQs
You can set up a Ransomware monitor like any other monitor, applied either at the device level or as part of a Monitoring policy. This includes the standard monitor settings (alert and response options) along with the option to isolate affected devices from the network and stopping suspected ransomware processes. Refer to Requirements and Ransomware monitor features.
If your Datto RMM account is integrated with Autotask PSA or ConnectWise Manage, then ransomware alerts created in Datto RMM can be configured to create tickets in those PSAs. Refer to Create a ticket.
Device isolation can be reverted by running the Revert Device Isolation [WIN] component available in the ComStore. This will revert any isolation that has occurred on a device and return its ability to contact the Internet and other devices on the network. Refer to Download a component.
The RMM Ransomware Detection engine looks for the existence of crypto-ransomware on endpoints using proprietary behavioral analysis of files.
You can run a simulation package to test Datto RMM Ransomware Detection. The simulation package (AutoRS.zip) and a set of instructions (Readme.txt) are available to download from here.
If you have suggestions or comments regarding the simulation package, please submit your feedback via the Send Feedback button from the New UI.
Datto RMM Ransomware Detection was tested by a third-party IT security testing firm. This included the following:
- Testing the effectiveness of Ransomware Detection against current in-the-wild strains of ransomware.
- False positive tests where Ransomware Detection was used alongside legitimate apps that mimic malicious ransomware behaviors.
- Performance testing to check impact on system performance for devices running Ransomware Detection.
To view the results, you can download the report from here.



